Lethal weapon against exploits: Kaspersky Labs corporate solution outstrips its competitors again30 April 2014 Kaspersky Lab’s security solution for corporate users Kaspersky Endpoint Security for Business once again proved its effectiveness in the Real World Enterprise Security Exploit Prevention Test carried out by MRG Effitas between November 2013 and February 2014. Exploits are malicious programs that utilize vulnerabilities (i.e., critical errors in the code) in legitimate software to penetrate a computer. An exploit usually affects the system when a user of vulnerable applications visits an infected web page. Any web page, even one that is familiar and has been safely visited before, can be infected. The exploit is activated without the user’s knowledge and does not require an executable file to download or run. For corporate users exploits are even more dangerous because an attack on a company’s computers can disrupt its business processes and lead to huge losses – both financial and reputational. The use of exploits drastically increases the efficiency of targeted cyber-attacks on organizations. One of the more recent examples is the Careto malware which hit at least 380 public and private targets worldwide. Protecting corporate clients is even more complicated because some companies have to use software that is only compatible with older – and consequently more vulnerable – versions of Java, for which the majority of exploits are written today. MRG Effitas investigated the level of anti-exploit protection provided by six corporate products from different vendors. Unlike its competitors, not only was Kaspersky Endpoint Security for Business tested as an integrated product but its Automatic Exploit Prevention module was also trialed in isolation from all other protection mechanisms. This anti-exploit technology is used in all Kaspersky Lab protection solutions. The experts at MRG Effitas selected 110 malicious links containing exploits to test the protection provided by the different products. The vast majority (98) of these exploits targeted the Java platform. The surge in their number over the last two years was the subject of the Kaspersky Lab study “Java under attack - the evolution of exploits in 2012-2013”. The testing was divided into two stages. The first stage determined the percentage of exploits blocked at an early phase, before the malicious code started its destructive activity. The second stage was less stringent and the security solution was awarded a “pass” if it failed to block the initial exploit but managed to counter any malware it tried to load. 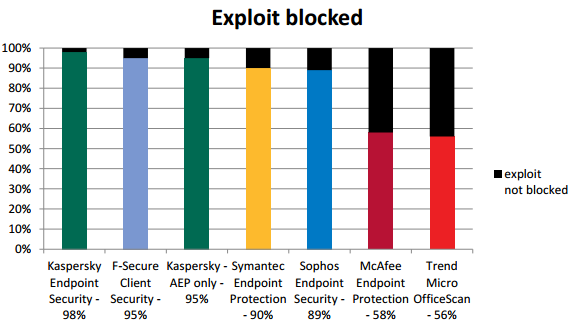 Kaspersky Endpoint Security for Business demonstrated the best results in the first stage blocking 98% of exploits. Even when Automatic Exploit Prevention was tested in isolation, without any other security features, the solution performed better than most of the other participants and shared second place after blocking 95% of the exploits. At the second stage Kaspersky Endpoint Security for Business blocked 100% of the threats. Only one rival product could match this result while the other participants scored no more than 94%. The results of the Real World Enterprise Security Exploit Prevention Test saw Kaspersky Lab’s corporate solution receive the MRG Effitas Certified award. Oleg Ishanov, Director Anti-Malware Research, Kaspersky Lab, commented: "To date, no serious cyber-attack targeting an organization can function without exploits. Acting as secretly as possible, exploits seize control of the computer and then run malicious code that unleashes the main part of the attack. So it is much safer to block the exploit at the first stage, before it can load malicious programs onto the computer. The MRG Effitas test demonstrated that our Automatic Exploit Prevention technology can cope with this task better than our competitors’ solutions even when isolated from the other security sub-systems in the product.” Testing was carried out on a 64-bit version of Microsoft Windows 7 Enterprise SP1. The applications which were most frequently targeted by exploits in the preceding year, such as Java 1.7, Adobe Reader 9.3, Flash Player 10.1, Silverlight 5.1 and Internet Explorer 8.0, were also installed on the test computers. |