Kaspersky Lab’s New Malware Count Falls by 15,000 a Day in 2015, as Cybercriminals Look to Save Money17 December 2015According to Kaspersky Lab, 2015 marked the moment when demand for new malicious programs reached saturation point, as the number of new malware files detected every day by its products fell by 15,000, from 325,000 in 2014 to 310,000. Kaspersky Lab’s experts believe this is mainly due to the fact that coding new malware is expensive and cybercriminals have realized that they can get equally good results using intrusive advertising programs or legitimate digital signatures in their attacks. This approach appears to be working, as results show that despite the cost-cutting in malware creation, in 2015 the number of users attacked by cybercriminals increased by 5%. 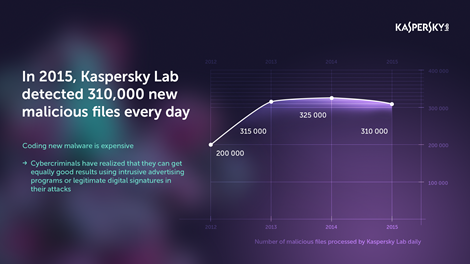 Between 2012 and 2013, there was a rapid increase in the number of new malicious files detected by Kaspersky Lab, from 200,000 new files every day in 2012 to 315,000 in 2013. Thereafter, things started to slow down. In 2014, the total increased by just 10,000 files a day, and in 2015 the overall number has declined from 325,000 to 310,000. Cybercriminals in search of a quick return appear to have decided that complex coding tools such as rootkits, bootkits or replicating viruses, may bring results, but at a cost, reducing their overall margins and revenue. Moreover, these complex malicious programs, that can cost tens of thousands of dollars to develop, do not protect the malicious program from increasingly sophisticated antivirus software accustomed to detecting and analyzing far more complicated malware. For this reason, 2015 saw adware, essentially harmless but often intrusive, become more prominent among overall anti-virus detections. This marks an evolution in cybercriminal tactics, with many now acting almost as businesses, engaged in selling quasi-legitimate commercial software, activity and other “essentials”. Another trend is for cybercriminals and even advanced, state-sponsored threat actors to make greater use of legal certificates for digital products. With the help of bought or stolen certificates, attackers deceive security software, which trusts an officially-signed file more than a regular one. The value of the certificate may be only a few tens of dollars. |